Assignment: Operating System
I. Quite a lot of computer systems do not make a provision for a privileged mode of operation in their hardware. Is it conceivable to design a secure operating system for these computer systems? Give arguments for and against.
II. With several definitions of operating systems, there is a contemplation whether operating systems should include applications such as notepad, paint etc. or not. Argue for both assertions and provide supporting arguments.
III. How does the kernel mode and user mode provide such form of security to the operating systems?
IV. Imagine you are designing an operating system, what key services would your operating system provide. In each service, provide whether user space programs can provide such services. Explain.
V. In what way is the difference between the kernel mode and user mode function as a basic principle of operating system protection.
VI. Direct Memory Access is used for high-speed I/O devices to reduce pressure on CPU's execution load.
1. In what way does the CPU interact with the device to coordinate data transfer
2. In what way does the CPU confirm if the memory operations are complete
VII. Provide arguments to and against to this assertion. Some computer systems do not offer hardware protection.
VIII. Explain the main advantage of separating mechanism from policy in operating system structures?
IX. In layered approach operating structures, it is quite difficult to be maintained if two layers are dependent on each other. Identify a scenario where it is difficult to structure layers that quite tight coupling
X. Explain the actions that are taken by a kernel during context-switching between processes
XI. On a single-processor system, explain the benefit the better performance of multi-threaded kernel threads over single threaded kernel threads
XII. But not parallelism, it is achievable to have concurrency in operating system threading?
XIII. The following processes are being scheduled using a priority (a smaller priority number implies a higher priority) and shortest job first all preemptive scheduling algorithms.
Process Priority Burst Arrival
P1 50 30 0
P2 40 35 25
P3 40 35 30
P4 45 25 60
P5 15 20 100
P6 20 20 105
1. Draw the Gantt charts that illustrate the execution of these processes using the above scheduling algorithms.
2. What is the turnaround time of each process for each of the scheduling algorithms in part a?
3. What is the waiting time of each process for each of these scheduling algorithms?
4. Which of the algorithms results in the minimum average waiting time (over all processes)?
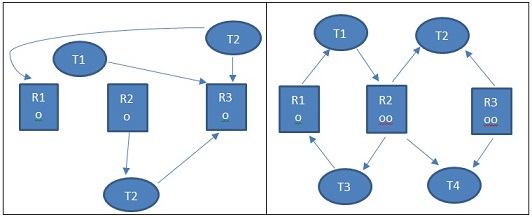
XIV. In the four diagrams illustrated below, show which of them result in deadlock? For those situations that will result in deadlock, provide the cycle of resources and threads. For those situations which are not in deadlock, show by illustration the order in which the threads may complete their executions
XV. Consider a logical address of 128 pages of 1024 words each, mapped onto a physical memory of 64 frames.
1. How many bits are there in the logical address?
2. How many bits are there in the physical address?
3. What is the size of the page table?
Format your assignment according to the give formatting requirements:
1. The answer must be double spaced, typed, using Times New Roman font (size 12), with one-inch margins on all sides.
2. The response also includes a cover page containing the title of the assignment, the course title, the student's name, and the date. The cover page is not included in the required page length.
3. Also include a reference page. The references and Citations should follow APA format. The reference page is not included in the required page length.