Assignment Task 1: Discrete mathematics in Computing
Assignment Outcomes:
A) Examine set theory and functions applicable to software engineering.
B) Analyze mathematical structures of objects using graph theory.
C) Investigate solutions to problem situations using the application of Boolean algebra.
D) Explore applicable concepts within abstract algebra.
Assignment Activity 1:
Part 1:
1. Let A and B be two non-empty finite sets. If cardinalities of the sets A, B, and A ∩ B are 72, 28 and 13 respectively, find the cardinality of the set A ∪ B.
2. If n(A - B) = 45, n(A ∪ B) = 110 and n(A ∩ B) = 15, then find n(B).
3. If n(A) = 33, n(B) = 36 and n(C) = 28, find n(A ∪ B ∩ C).
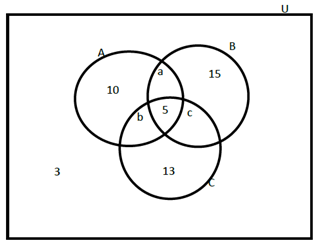
Part 2:
1. Write the multi-sets of prime factors of given numbers.
I. 160
II. 120
III. 250
2. Write the multiplicities of each element of multisets in part 2(1-I,ii,iii) separately.
3. Find the cardinalities of each multiset in part 2-1.
Part 3:
1. Determine whether the following functions are invertible or not. If it is invertible, then find the rule of the inverse (f-1(x))
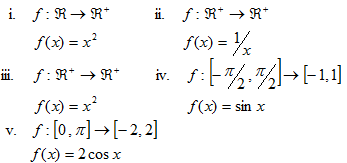
2. Function f(x) = 5/9 (x-32) converts Fahrenheit temperatures into Celsius. What is the function for opposite conversion?
Part 4:
1. Formulate corresponding proof principles to prove the following properties about defined sets.
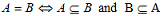
i.
ii. De Morgan's Law by mathematical induction.
iii. Distributive Laws for three non-empty finite sets A, B, and C.
Assignment Activity 2:
Part 1: Discuss using two examples on binary trees both quantitatively and qualitatively.
Part 2:
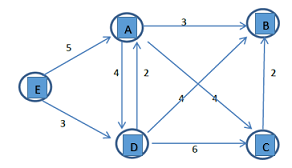
1. State the Dijkstra's algorithm for a directed weighted graph with all non-negative edge weights.
2. Find the shortest path spanning tree for the weighted directed graph with vertices A, B, C, D, and E given using Dijkstra's algorithm.
Part 3: Check whether the following graphs have an Eulerian and/or Hamiltonian circuit.
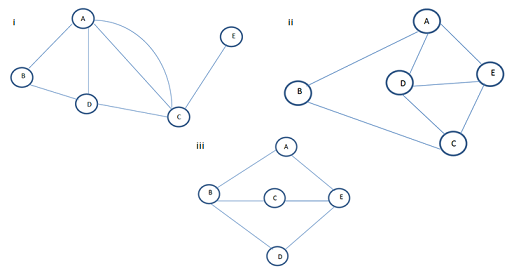
Part 4:
1. Construct a proof for the five color theorem for every planar graph.
2. Discuss how efficiently Graph Theory can be used in a route planning project for a vacation trip from Colombo to Trincomalee by considering most of the practical situations (such as millage of the vehicle, etc.) as much as you can. Essentially consider the two fold,
- Routes with shortest distance (Quick route travelling by own vehicle)
- Route with the lowest cost
3. Determine the minimum number of separate racks needed to store the chemicals given in the table (1st column) by considering their incompatibility using graph coloring technique. Clearly state you steps and graphs used.
|
Chemical
|
Incompatible with
|
|
Ammonia (anhydrous)
|
Mercury, chlorine, calcium hypochlorite, iodine, bromine, hydrofluoric acid (anhydrous)
|
|
Chlorine
|
Ammonia, acetylene, butadiene, butane, methane, propane, hydrogen, sodium carbide, benzene, finely divided metals, turpentine
|
|
Iodine
|
Acetylene, ammonia (aqueous or anhydrous), hydrogen
|
|
Silver
|
Acetylene, oxalic acid, tartaric acid, ammonium compounds, pulmonic acid
|
|
Iodine
|
Acetylene, ammonia (aqueous or anhydrous), hydrogen
|
|
Mercury
|
Acetylene, pulmonic acid, ammonia
|
|
Fluorine
|
All other chemicals
|
Assignment Activity 3:
Part 1: Discuss two real world binary problems in two different fields using applications of Boolean algebra.
Part 2:
1. Develop truth tables and its corresponding Boolean equation for the following scenarios.
i. ''If the driver is present AND the driver has NOT buckled up AND the ignition switch is on, then the warning light should turn ON.''
ii. If it rains and you don't open your umbrella then you will get wet.
2. Produce truth tables for given Boolean expressions.
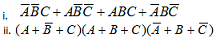
Part 3: Find the simplest form of given Boolean expressions using algebraic methods.
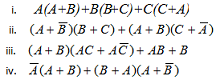
Part 4:
1. Consider the K-Maps given. For each K- Map.
i. Write the appropriate standard form (SOP/POS) of Boolean expression.
ii. Draw the circuit using AND, NOT and OR gates.
iii. Draw the circuit only by using
- NAND gates if the standard form obtained in part (i) is SOP.
- NOR gates if the standard form obtained in pat (i) is POS.
(a)
|
AB/C
|
0
|
1
|
|
0
|
0
|
0
|
|
1
|
0
|
1
|
|
11
|
0
|
1
|
|
10
|
1
|
0
|
(b)
|
AB/CD
|
0
|
1
|
11
|
10
|
|
0
|
1
|
0
|
0
|
1
|
|
1
|
0
|
1
|
0
|
1
|
|
11
|
1
|
1
|
1
|
0
|
|
10
|
1
|
1
|
1
|
1
|
(c)
|
AB/C
|
0
|
1
|
|
0
|
1
|
0
|
|
1
|
1
|
1
|
|
11
|
1
|
0
|
|
10
|
0
|
1
|
Assignment Activity 4:
Part 1:
1. Describe the characteristics of different binary operations that are performed on the same set.
2. Justify whether the given operations on relevant sets are binary operations or not.
i. Multiplication and Division on se of Natural numbers
ii. Subtraction and Addition on Set of Natural numbers
iii. Exponential operation: (x, y) → xy on Set of Natural numbers and set of Integers.
Part 2:
1. Build up the operation tables for group G with orders 1, 2, 3 and 4 using the elements a, b, c, and e as the identity element in an appropriate way.
2. i. State the Lagrange's theorem of group theory.
ii. For a subgroup H of a group G, prove the Lagrange's theorem.
iii. Discuss whether a group H with order 6 can be a subgroup of a group with order 13 or not. Clearly state the reasons.
Part 3:
1. Check whether the set S = R - {-1} is a group under the binary operation '*'defined as a * b = a + b + ab for any two elements a, b ∈ S.
2. i. State the relation between the order of a group and the number of binary operations that can be defined on that set.
ii. How many binary operations can be defined on a set with 4 elements?
3. Discuss the group theory concept behind the Rubik's cube.
Assignment Task 2: Network Security - Higher National Diploma in Computing
Course Learning Outcomes:
1) Examine Network Security principles, protocols and standards.
2) Design a secure network for a corporate environment.
3) Configure Network Security measures for the corporate environment.
4) Undertake the testing of a network using a Test Plan.
Assignment Brief and Guidance:
EMC Finance is a well-known Finance company established in Kandy with more than 5000 customers and 8 branches island wide. Director board of EMC Finance has decided to restructure and enhance the computer network at Head office with up to date security measures to face the emerging security threats worldwide. You have been appointed as the Network Security Engineer for EMC Finance and it is now your responsibility to plan and implement a secure network that fulfils the company's expectations.
Main requirements are as follows but NOT limited to;
1. Head office LAN need to be a Gigabit Ethernet and all Network devices need to be compatible with each other for maximum performance.
2. All the network devices such as Routers, Switches, Firewalls etc. should be manageable and only secure logins need be allowed on all devices.
3. AAA should use for Network Device login Authentication where possible and Syslog Server should use for record logging events, while having NTP server for time.
4. All publicly available resources including public web servers need to be separated from the main network and should move to a separate subnet. Only Secure Web Access should be enabled for web servers.
5. Design a SAN (Storage Area Network) implementation for saving Data for the Internal Network.
6. Network design should follow the Hierarchical Network Design Model.
7. End user authentication and managing of security polices need to centralized.
8. Internet usage management and URL filtering need to be enforced.
9. Communication between the Head office and the Branch offices need to be highly secured.
10. Quality of service (QoS) should be implemented where possible.
EMC Finance Head office consists of the following departments:
|
Department
|
Number of Users
|
|
Customer Care
|
25
|
|
Sales and Marketing
|
35
|
|
Finance
|
60
|
|
Legal
|
5
|
|
HR
|
20
|
|
IT Team
|
25
|
|
Internal Server Room
|
8 Servers + SAN
|
|
Servers for Public users
|
4
|
Task 1: Examine Network Security principles, protocols and standards.
A) Discuss the importance of Network Security in present socio-economic world.
B) Describe devices and their characteristics that are used to enhance the security of a Network.
C) Differentiate Symmetric and Asymmetric Encryption with examples.
D) Explain the purpose of a Digital Certificate in secure web access.
Task 2: Design a secure network for a corporate environment.
A) Provide a suitable Virtual LAN design for internal network and IP Design for the network. (Public servers should be separated from the Internal Network)
B) Explain the Technologies /concepts that are required to accomplish the objectives of the above scenario.
C) Determine which security devices and software are needed to design this network and justify your selections.
D) Provide a suitable detailed Diagram of above Network Design including WAN connections.
Task 3: Configure Network Security measures for the corporate environment.
A) Configure all the network devices to achieve the highest level of security for the network with the requirements given by the scenario.
(Provide Network Security configuration scripts/files/screenshots with comments.)
B) Explain how QoS can be integrated in to Network security configurations.
Task 4: Undertake the testing of a network using a Test Plan
A) Develop test cases and test the above LAN and WAN designs to verify whether the design objectives are met.
(Provide Network Security configuration scripts/files/screenshots with comments.)
B) Suggest how you can improve the performance and security of this network in the Future.
Assignment Task 3: Transport Network Design - Higher National Diploma in Computing
Course Learning Outcomes:
A) Explore LAN design principles and their application in the network design process
B) Implement a network using LAN design principles based on a predefined set of requirements
C) Produce an appropriate WAN solution to a set of organizational requirements
D) Solve a range of network related problems using appropriate troubleshooting techniques and methods
Assignment Brief:
EMC Solutions is a private owned well-known Software company located at Colombo. The Management of EMC Solutions decided extends their services Kandy and as a result building with 3 stories has purchased in the heart of Kandy town. They are planning make it to become one of the state-of-the-art companies in Kandy with new facilities.
They are expecting have nearly 150 employees in Kandy branch.
Following requirements are given by the Management;
- All departments must be separated with unique subnet and should not communicate each other unless special requirements are given.
- 10.254.1.0/24 is given and should use for all the departments except Server Room. IPs should assign using DHCP.
- Server Room and SAN should be in 192.168.1.32/27 subnet. (Uses static IPs)
- High level of redundancy is expected in network design to eliminate the single point of failures and traffic bottle necks.
- Multiple ISP connections need to configure for gateway redundancy.
- Link aggregation need to configure to improve the Network performance where necessary.
- Data transmission between Head office and Kandy need to be secured with proper WAN design.
- Sales and Marketing Team need to access resources at Kandy office and the head office securely while they are in field visits.
- Proper methods for networking monitoring and troubleshooting need to be established.
- Customer Care and Sales team should not be allowed to access the Finance Web server in Kandy server Room.
- All possible network security mechanisms should be implemented.
Task 1: Explore LAN design principles and their application in the network design process.
A) What do you mean by Network Design Model and explain the importance of having Network Design Models for proper network design? (Three layer models details)
B) Suggest a network design model for above scenario and justify your suggestion. ( Why are you choosing three layer model )
C) Explain the importance of Layer 2 redundancy and describe Layer 2 redundancy protocols use in industry and recommend protocol/protocols for above scenario and justify your selection. (Switch redundancy, What is STP, What should do STP) , l2 redundancy and l3 redundancy
D) Explain the importance of Link Aggregation and describe Link Aggregation protocols use in industry and recommend protocol/protocols for above scenario and justify your selection. (Ether Channeling / PAGP and LCAP meaning)
E) Explain the importance of Layer 3 redundancy and describe Layer 3 redundancy protocols use in industry and recommend protocol/protocols for above scenario and justify your selection. Click Here HSRP/VRRP/GLBP
Task 2: Implement a network using LAN design principles based on a predefined set of requirements
A) Provide list of Network Devices and justify your selections for above Network Design. (Switches/Router/Firewall and examples)
B) Provide IP Subnet Design for the Kandy Branch
C) Provide Complete Network Diagram Including WAN for above scenario according to your design.
Cisco 2811 , Switches 3560 2160
D) Configure all the network devices with basic configurations*.
E) Implement and configure All required Layer 2 and Layer 3 solutions (including redundancy) * to Kandy Branch LAN according to the requirements given in the scenario.
Task 3: Produce an appropriate WAN solution to a set of organizational requirements.
A) Describe various WAN technologies with their characteristics, which are used in industry and protocols associated with them and select WAN Technology for given scenario and justify your selection. (ATM, MPLS, Frame relay, X. 25,) , What is it? Advantage and disadvantage
B) Implement and Configure * the selected WAN technology to above Network.
Ex - Colombo to Matara Connectivity, VPN - Client to client and Site to Site
Task 4: Solve a range of network related problems using appropriate troubleshooting techniques and methods.
A) Explain the importance of Network monitoring related to LAN and WAN.
B) Describe few Network Monitoring Tools and Protocols, which are used in industry with their characteristics. (3 tools example minimum Whatsup, Nagios/ SCOM )
C) Implement and Configure* selected Network Monitoring Tool/Tools to above Network.
D) Develop test cases and Test the above LAN and WAN* designs to verify whether the design objectives are met. (Ping , Trace )
E) Explain and document the troubleshooting steps following scenarios;
i) Kandy branch users cannot access the resources in server located at Colombo Head office.
ii) Customer Care users can access File Servers at Kandy branch but Sales and Marketing users cannot access the same Servers but can access the Internet.
Discrete mathematics in Computing Assignment Help Homework Help service has everything that you look for to keep your academic grades ahead.
Tags: Discrete mathematics in Computing Assignment Help, Discrete mathematics in Computing Homework Help, Discrete mathematics in Computing Coursework, Discrete mathematics in Computing Solved Assignments, Boolean Algebra Assignment Help, Boolean Algebra Homework Help, K-Maps Assignment Help, K-Maps Homework Help, Graph Theory Assignment Help, Graph Theory Homework Help, Dijkstra's Algorithm Assignment Help, Dijkstra's Algorithm Homework Help, De Morgan's Law Assignment Help, De Morgan's Law Homework Help
Attachment:- Transport Network Design.rar
Attachment:- Network Security.rar