Problem 1: Consider Lamport's Scheme for authentication. Suppose the parameter n=100.
(a) A crash can potentially cause the server to be out of synchronization with the user. For example, suppose after a crash, the server is storing h50(k), but a user Alice has become out of synchronization with the server, so she may either send in an earlier value such as h53(k), or a later value such as h47(k) for authentication. The authentication would fail in both cases, if the server does not know Alice is out of synchronization. Fortunately, the Lamport's scheme would allow the server to detect an out-of-synchronization user in either case. Please describe in details: 1.) how the server could detect that Alice is out of synchronization, and 2.) Alice is in which of the two cases (that is, is she sending h51(k) or h47(k)?).
b) Suppose an attacker is passively sniffing all the traffic between Alice and the server. For those two cases (Alice is sending either h51(k) or h47(k)), the server should take very different actions to ensure security. What are those actions? And Why? Please explain
Problem 2: Take the last four digits of ( 40104446) as the amount of storage available (e.g., if the number was 12345678 then the available storage would be 5678, that is, you could store at most five thousand six hundred and seventy eight password/hash values). Suppose every password can be 3 to 5 characters long, and each character can be either a lower or upper case English letter (A-Z) or number (0-9). How many columns should your Time Memory Tradeoff table. Please provide detailed explanation
Problem 3: Consider the simplified boot process shown in the picture.
(a) Suppose the hash function is collision free and the BIOS can never be compromised. If we modify the AEGIS architecture such that level i+1 will compute and store the hash of level i+2after leveli has already computed and stored the hash of level i+1, how could an attacker modify the OS without being detected, and why?
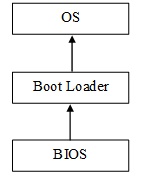
b. Following 3(a), even if we use digital signatures instead of hash function (assuming the digital signature and private key are perfectly secure), the attackers could still modify the OS without being detected. Please explain why
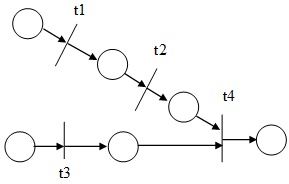
Given the following Colored Petri Net, list all sequences of those events that will not be detected as attacks.