Assignment: Cyber Security Principles
Learning Outcomes
Students should be able to demonstrate their achievements in the following unit learning outcomes:
a. Understand the Common Security Countermeasures
b. Managing security programs, and design a secure Network Topology.
Part A description:
Topic - infrastructure can be limited to one location or, widely distributed, including branch locations and home offices. Access to the infrastructure enables the use of its resources. Infrastructure access controls include physical and logical network design, border devices, communication mechanisms, and host security settings. Because no system is perfect, access must be continually monitored; if suspicious activity is detected, a response must be initiated.
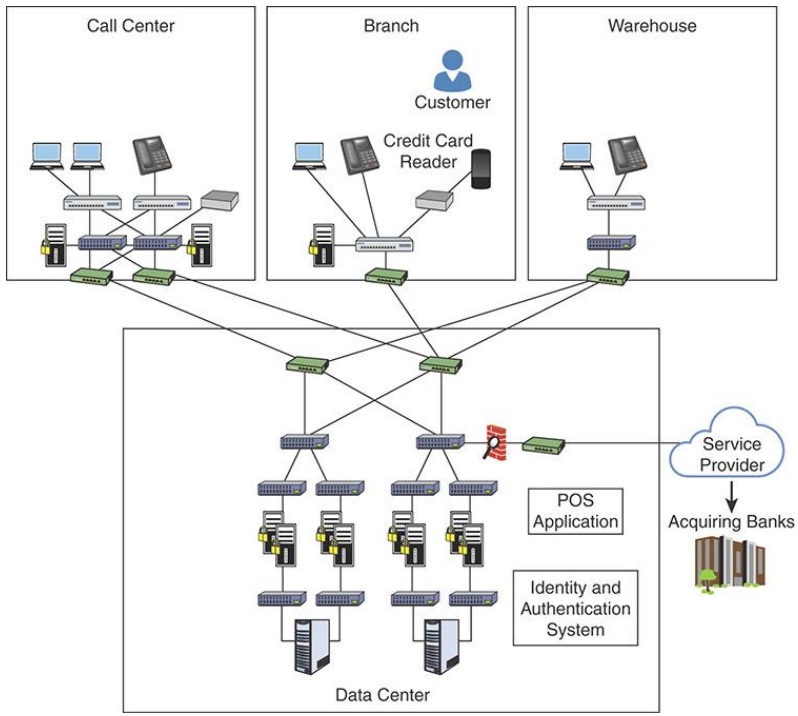
Figure 1 shows the topology of a network that has not been properly segmented.
The network topology consists of a Call center, a Branch, a Warehouse, and a Data center.
• The Call center shows two file servers, one application server, and a database server that is connected together directly and diagonally. The file server on the left is connected to two laptops and the file server on the right is connected to a telephone. The application server is connected to two servers on the right and left and to a switch.
• The Branch consists of a file server that is connected to a laptop, telephone, and to a switch that is further connected to a credit card reader at the top and to a server on the right and to a database server at the bottom.
• The Warehouse consists of a file server that is connected to a laptop and a telephone at the top, an application server at the bottom that is further connected to a database server at the bottom. The database server of the call center, branch, and the warehouse are connected to the two database servers of the data center.
• The data centers are connected to two application servers directly and diagonally. The application servers are connected to two database servers at the bottom and to a firewall on the right that is further connected to a switch. The application servers are connected to the "POS Application" consisting of a set of two servers that are connected to each of the application servers. Each server is again connected to the "Identity and Authentication System" consisting of two application servers on the right and two servers on the left. The two application serves on the left and right are connected to two servers. The switch at the top is connected to a service provider that is further connected to acquiring banks.
You need to cover the following topics
Why Segment a Network?
Working from the inside out, network segments include the following types:
• Enclave network: A segment of an internal network that requires a higher degree of protection.
• Trusted network (wired or wireless): The internal network that is accessible to authorized users.
• Semi-trusted network, perimeter network, or DMZ: A network that is designed to be Internet accessible. Hosts such as web servers and email gateways are generally located in the DMZ.
• Guest network (wired or wireless): A network that is specifically designed for use by visitors to connect to the Internet.
• Untrusted network: A network outside your security controls. The Internet is an untrusted network.
1. Security Consideration when segmenting a network:
a. Apply security measures to secure the access of internal network.
b. Apply security measures to secure the access of external network.
c. Apply security measures to secure the access of perimeter network.
d. Apply security measures to secure the access of guest network.
e. Apply security measures to secure the access of data sent over public network.
Securing the Network Topology: The network topology in Figure 1 shows an enterprise that has a call center, a branch office, a warehouse, and a data center. The branch is a retail office where customers purchase their goods and the enterprise accepts credit cards. Users in the call center and the warehouse have access to the resources in the Branch office and vice versa. They also have access to resources in the data center. If any device is compromised, an attacker can pivot (or move laterally) in the network.
2. List all assets at the branch and call centre, and assess the vulnerability associated with these assets assuming that database server is based on SQL, and file servers and application servers are running at Window server platform.
3. You need to redesign this network by adding relevant Firewalls to allow the traffic from the credit card readers to communicate only with specific servers in the data center. Draw a diagram to show the location of the proposed firewalls and explain their roles. (Note you need to consider securing the access at different levels as described in network segmentation above)
a. Firewall can be based on content filtering or other techniques. Explain the role of Content Filtering and Whitelisting/Blacklisting. Comment on which section (call centre, branch, and warehouse) this content firewall would be helpful.
4. Explain the role of Border Device Administration and Management that can be used to enhance the network security.
5. Different role of security team such as Blue, Red, and Purple can have impact of the network security.
Creating a Request for RFP for Penetration Testing
You have been asked to send out a red team penetration testing Request for Proposal (RFP) document.
a) Explain what is often referred to as a "red team."
b) Explain the difference between a red team and a blue team.
c) Find three companies to send the RFP to. Explain why you chose them.
d) The selected vendor will potentially have access to your network. Describe the due diligence criteria that should be included in the vendor selection process. Select one of the companies from the previous step and find out as much as you can about them (for example, reputation, history, credentials).
6. Access Control:
a. Explain the role of Border Device Security Access Control Policy
b. Explain the remote access security policy.
c. Develop a relevant User Access Control and Authorization Policy
d. The following example Role-based access controls (RBACs) (also called "nondiscretionary controls") are access permissions based on a specific role or function. Administrators grant access rights and permissions to roles. Users are then associated with a single role. There is no provision for assigning rights to a user or group account.
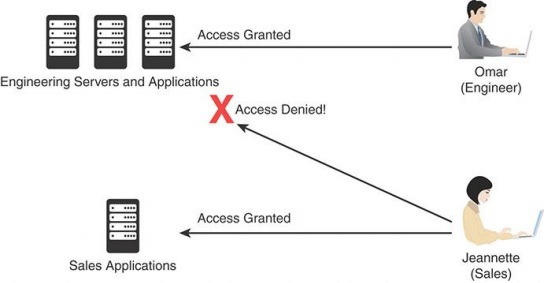
Let's take a look at the example illustrated in Figure 2
In the sample "Omar (Engineer)" is shown at the top right and "Jeannette (Sales)" is shown at the bottom right. The Access is granted to three Engineering Servers and Applications at the top left from the Omar. From Jeannette, the Access is granted to the Sales Applications at the bottom left and the Access is denied to the Engineering Servers and Applications.
i. Explain why Omar can access the Engineering servers and applications but not Jeannette.
ii. Give examples on how to implement Role-based access controls in Windows and Linux
7. Explain a relevant Monitoring System Access and Use Policy
Reviewing user access permissions can be a time-consuming and resource-intensive process and is generally reserved for applications or systems that have information classified as "protected" or "confidential."
a) Comment if student portal at your school would be subject to an annual user access permission audit or not and why.
b) Automating review processes contributes to efficiency and accuracy. Research options for automating the user access review process and make a recommendation.
8. Researching a DDoS Attack:
a. Find a recent news article about DDoS attacks.
b. Explain who were the attackers and what was their motivation.
c. Describe the impact of the attack, and what should the victim organization do to mitigate future damage.
9. Analyze the network availability at the Datacenter and develop a Business Continuity plan to handle a possible crisis associated with flood or earthquake.
Reference: Sari Greene, Omar Santos, "Developing Cybersecurity Programs and Policies, Third Edition", Pearson IT Certification, July 2018.
Part B description: Prepare 5 slides for presentation during the lab class. Read the instruction attached carefully.
Format your assignment according to the following formatting requirements:
1. The answer should be typed, double spaced, using Times New Roman font (size 12), with one-inch margins on all sides.
2. The response also includes a cover page containing the title of the assignment, the student's name, the course title, and the date. The cover page is not included in the required page length.
3. Also include a reference page. The Citations and references should follow APA format. The reference page is not included in the required page length.