Assignment Problem: Secure Network Design and Implementation
Assignment Aim: This assignment assesses the following
Unit Learning Outcomes; students should be able to demonstrate their achievements in them.
A) Describe architectural VPN design for small, medium and large businesses and corporations
B) Report on the health of the existing VPN architecture, solution, data, application, and technology
C) Discuss the appropriate security design and solutions for varieties of organisations
D) Report on the current and future state of the management of VPN infrastructure and its technologies
E) Interpret a roadmap process to transform the VPN architecture to support long- term organizations' goals
F) Implement a process to support the administration and the management of VPNAssignment Description
Assignment Tasks:
There are two parts to this assignment, i.e. part A and part B.
1. Investigate, design and develop a suitable VPN network for a fictitious company in Australia (CyberVision Inc.) by addressing the following criteria. See detailed instruction in the next section.
2. Presentation.
Part A description:
Situation
Many companies use frame relay or leased lines to provide secure communications with their business partners, subsidiaries, and vendors. Unfortunately, these solutions are often expensive and geographically limiting. VPN offers an alternative for companies who want private, cost-effective communications.
Suppose you are a major parts supplier to a manufacturer. Since it is critical that you have the specific parts and quantities at the exact time required by the manufacturing firm, you always need to be aware of the manufacturer's inventory status and production schedules. Perhaps you handle this interaction manually today, and find it time consuming, expensive and even inaccurate at times. You want to find an easier, faster, and more effective way to communicate with your manufacturing company. However, given the confidentiality and time-sensitive nature of the information you exchange, the manufacturer does not want to publish it on its corporate Web site or distribute it monthly in an external report. By exploiting the public Internet, you can easily establish a VPN to meet the needs of both companies.
Objectives:
In this scenario, MyCo wants to establish a VPN between a host in its parts division and a host in the manufacturing department of one their business partners, TheirCo.
Because the information these two companies share is highly confidential, it must be protected while it travels across the Internet. In addition, data must not flow in the clear within either company's networks because each network considers the other untrusted. In other words, both companies require end-to-end authentication, integrity, and encryption.
Details:
The following figure illustrates the network characteristics of MyCo and TheirCo:
Details:
The following figure illustrates the network characteristics of MyCo and TheirCo:
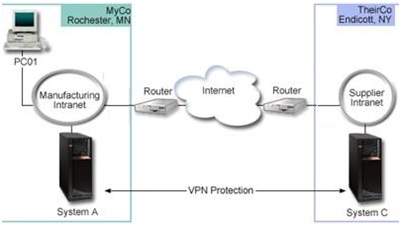
Figure: MyCo and TheirCo network setup
MyCo Supply Network:
- System A has an IP address of 10.6.P.1. This is the connection endpoint, as well as the data endpoint, whereas P is number composed of last two (FIFTH and SIXTH) digit from your MIT ID number. That is, System A performs IKE negotiations and applies IPSec to incoming and outgoing IP datagrams and is also the source and destination for data that flows through the VPN.
- System A is in subnet 10.6.P.0 with mask 255.255.0.0
- Only System A can initiate the connection with System C.
TheirCo Manufacturing Network:
- System C has an IP address of 10.196.Q.8 , whereas Q is number composed of THIRD and FOURTH digit from your MIT ID number This is the connection endpoint, as well as the data endpoint. That is, System C performs IKE negotiations and applies IPSec to incoming and outgoing IP datagrams and is also the source and destination for data that flows through the VPN.
- System C is in subnet 10.196.Q.0 with mask 255.255.255.0
Your Tasks:
1. Design a network for MyCo and TheirCo Inc.
2. Build VPN services for the users. The network solution would be built on a simulator i.e CISCO Packet tracer and include establishing a VPN from two sites as discussed above.
Report must include:
- Introduction
- Scopes and Limitations
- Requirements (Network parts and VPN service parts)
- Solution Design
o Logical Design
o Physical Design
o Network Topologies
o IP addressing
o Security features and Policies
o Redundancy and Failover plans
o VPN service Deployment and implementation
- Refer the sample document included in below for network design, and consider how to deploy and implement relevant VPN services onto the network. You need to choose the right type of VPNs and protocols that satisfy the requirements for remote and branch to branch connectivity.
Part B description:
Presentation slides should be submitted in Moodle prior to the presentation for marking. No other options (e.g. hard copy, memory stick, website, email etc) will be considered but the presentation file submitted in Moodle. Students need to demonstrate their work in Lab 11. The demonstration will include viva voce (oral test) questions as well.
Preparing a good quality assignment paper based on above is not a cakewalk and for that reason, it is always advisable to take Secure Network Design and Implementation Assignment Help service for better academic grades.
Tags: Secure Network Design and Implementation Assignment Help, Secure Network Design and Implementation Homework Help, Secure Network Design and Implementation Coursework, Secure Network Design and Implementation Solved Assignments, Virtual Private Networks Assignment Help, Virtual Private Networks Homework Help
Attachment:- Secure Network Design and Implementation.rar