Assessed Learning Outcomes
1 Design a small routable network comprising LAN and WAN components
2 Configure routers to implement small routable networks
Scenario
You are a network engineer for a UK based travel agency (UKTA) which has the following network topology:
Topology
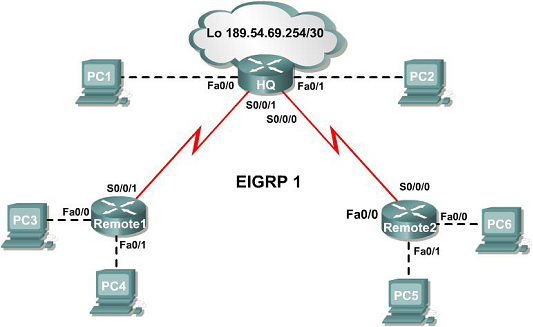
Configuration Tasks
You are required to configure the above topology to meet the following requirements:
1. Using the network address 192.168.156.0/22, create an addressing scheme to accommodate all hosts on the network as follows:
|
Device
|
Interface
|
Number of Hosts
|
|
HQ
|
Fa0/0
|
90
|
|
Fa0/1
|
60
|
|
S0/0/1
|
2
|
|
S0/0/0
|
2
|
|
Remote1
|
Fa0/0
|
30
|
|
Fa0/1
|
60
|
|
S0/0/1
|
2
|
|
Remote2
|
Fa0/0
|
128
|
|
Fa0/1
|
60
|
|
S0/0/0
|
2
|
2. Configure EIGRP with AS Number 1.
Configure EIGRP on the HQ router and advertise all connected networks except the loopback interface
Configure EIGRP on Remote1 and Remote2 and advertise all connected networks.
3. Configure a static default route on the HQ router to the loopback interface. Propagate the default route through out the AS.
Testing
1. Write a detailed test plan to thoroughly test and verify your configuration.
2. Produce suitable test results based on the above test plan.
Bandweth
- Bandweth calculating
Deliverables
A written report containing the following, but not exhaustive, sections:
- Detailed Design including justifications
- Detailed addressing scheme
- Configuration files, one per page
- Detailed Test Plan and Test Results
- Packet Tracer files (on a CD)
Grade Criteria
Marks will be awarded based on the Anglia generic assessment criteria for a Level 2 module (see Module Guide for full details). However, the following guidelines should assist students in their assignment planning:
1. Valid addressing scheme with correct usage of subnet masks and interfaces addresses
2. Accuracy of router configurations to include global and router configuration
3. Quality of test plan and relevant test results
4. Report presentation quality