1. Summarize what is being accomplished in this section in a few sentences.
What is being accomplished here is that we have created a sequence generator that outputs two short random messages. The multiple sequence source generates two PN sequences that we are watching on the oscilloscope.
2. Use the two oscilloscope channels (ch A and ch B) to display TTL X and TTL Y of the Message Sequence Generator module. Are these identical? Should they be? Could they be?
The two signals that we are looking at are not identical.They should not be identical because we are generating two different random signals. They technically could be the same but the chances of that are very very slim so no they really could not be identical.
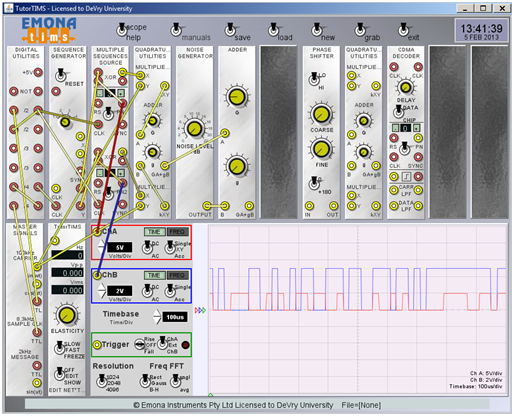
3. Display the multiple sequence generator output. Are these binary? Should they be?
Yes, these waveforms are a binary sequence. These outputs on the multiple sequence generator are our PN sequences. PN sequences are a sequence of binary numbers which appears to be random, but in fact perfectly deterministic.
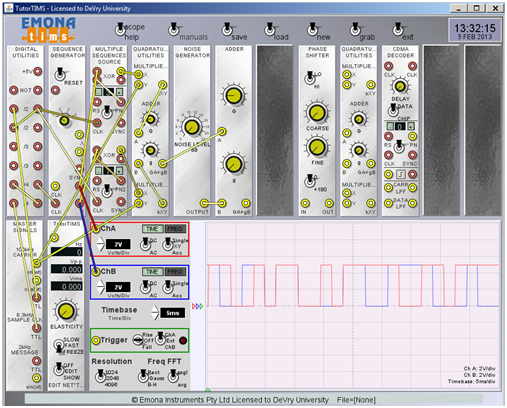
4. When the bit rate of a message signal from the message sequence generator and the bit rate of a PN code from the multiple sequence generators are compared, which is higher? How did you compare them? Could you determine by how much the bit rate of one is higher?