The passwords are hard-to-keep in mind strings of number and letters are highly insecure and inept to manage. The best to manage and remember password is biometric authentication, a innovative practice of using exclusive behavioural and biological traits like fingerprints, walk and ear shape to verify the identity.
Biometrics is still long way from replacing password -- they have twists which should be ironed out, and creating them work with present systems will take some time. There are also severe privacy worries to consider when it comes to gathering information in databases which would recognize people.
Five biometrics which are part of identification technologies are given below:
Heartbeat
Activity of Heart and its electrical signals are different and extremely hard to duplicate. Technology for reading the individual-s electrocardiographic signals has been there for many years, but new progressions have reduced sensing devices to small sizes and made them less persistent.
Somewhat as common as wearable fitness device or delicate as the flat pad implanted on to side of a Smartphone can sense person's heart rate. Apple has even applied for patent on embedded heart rate monitor for iPhone.
One another product in development is Nymi wristband. It seems like fitness band, but in its place counting steps it senses your heartbeat to verify your identity.
Twist is that it is not utilizing your cardiac rhythm to unlock one device. Nymi is developed to act like substitute for physical keys and passwords by wirelessly verifying your identity to front door, Smartphone, computer, vehicle and even stores. It can also distinguish motions, so that you can open home with wave.
Ear shape

Sensitive touch screens can choose much more than finger tap or swipe. With right software and phone, they can sense shape of human ear.
That is the idea behind Ergo Android application by Descartes Biometrics. When the ear is pressed against screen, points where it gets in touch with glass are mapped out and compared to stored ear print. If it matches, user is genuine. The app is adaptable and can need multiple scans for highest levels of security, or just one for people who think they have low risk of losing their phones.
For now, it is limited to unlock phone, but in theory ear could be utilized to recognize people for any number of uses on phone, like making purchases in app stores or signing in services.
There are potential advantages of using ear prints over fingerprints. The size of ear means it can be scanned utilizing live technology. There is no requirement to pay for devoted fingerprint sensor. It is also possible to understand the ear shape from the image, something which could advantage law enforcement working with observation photos or videos.
Fingerprints can also alter over time as people work with their hands, get injured and age. Advocates for ear biometrics claim which ears do not alter nearly much over course of lifetime.
Walk
If you have ever paid attention to someone walking past in office and right away known who it was, or spotted friend from distance by way they moved, you have already seen power of walk identification.
For thirty years, researchers have tinkered with walk-recognition technology by using high-resolution videos and particular floors which sense pressure. Recent boom in reasonably priced motion sensors such as accelerometers and gyros have given new life to field. Wearable fitness device or Smartphone moves along with body when you walk. Most of it is already counting steps and speed. With right software and sensors, they must be able to analyze person's walk and decide if they are rightful owner of devices.
Advantage of walk recognition is that it can collect essential information in background as people go about normal routines.
Typing speed
Typing differs from person to person. Keystroke biometrics evidence how person types and computes their exclusive pattern, speed and pace. It find out how long they hold down each key and space of time between different letters.
Keystrokes used to verify anyone working on the computer, so system could request to companies which are watching out for unlawful users on their internal systems.
Face recognition
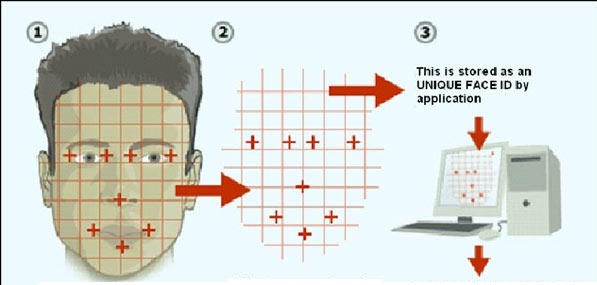
Face recognition is being used in well-liked technology. For facial recognition to do well, devices require a clear, sharp image to work with. Cameras in smart phones and tablets have enhanced radically and are on par with what you will discover in many point-and-shoot cameras. Software looks for patterns on human face, like distance between eyes, to recognize people.
Samsung is one company which has taken benefit of enhanced camera technology and it now has face-recognition unlock characteristic on its smart phones.
Security is immense for consumers, but it is not main goal of most facial-recognition tools. Law enforcement is building facial recognition databases. Recognizing one person by using their trail of selfies left online and in inspection footage from stores could be enormous business.